Like an ingrained trail of breadcrumbs, every click, post, and share leaves an imprint that shapes your virtual identity. It demands that you consciously consider safeguarding your digital persona by engaging authentically on social media while preserving boundaries.
In this article, we explore the realms of social media safety, unveiling digital footprint safety tips for a safer and smarter digital experience.
What is a Digital Footprint?
A digital footprint refers to the trail of data and information left behind after engaging in various online activities. It includes your online behavior, cyber presence, and web preferences. Essentially, it’s a shadow of one’s online presence and interactions.

Social media platforms display and remember your uploads, likes, and comments while emailing services record our contacts and messages. Over time, this accumulated data can build a comprehensive profile of an individual’s online behavior, preferences, and activities.
Types of Digital Footprints
- Active: Active digital footprints are intentionally created by individuals while engaging in online activities. It includes posting on social media, commenting on forums, writing blog posts, participating in online discussions, and sharing content.
- Passive: Passive digital footprints are generated without your knowledge. It is achieved through data collection by third-party browsing history, cookies, IP address logs, and online purchases tracked by websites and advertisers.
- Private: Private digital footprints consist of information shared only with a select group. For instance, text messages are shared in a private chat group.
- Public: Public digital footprints comprise information intentionally shared with a wide audience or accessible to the public.
Examples of Digital Footprints
- IP Addresses. Your device is assigned an IP address whenever you connect to the internet. This unique identifier can be used to trace your location and execute cyber crime and compelling scams.
- Browsers. Your web browser exchanges your information with websites, leaving a digital footprint, including browsing history, cookies, and cache.
- Shopping Sites. Your online shopping activities leave a digital trail, including the brands you support and the products you view and purchase.
- Social Media. Your social media profiles and activities contribute to a significant digital footprint, including posts, likes, comments, and friend lists.
- Emails. Your email communications, including sent and received messages, attachments, and contacts, create a digital footprint.
- Trackers. Every app that tracks you also generates your information, creating digital footprints. They include fitness trackers, time trackers, and reading trackers.
- Blog Posts. Publishing or commenting on blog posts leaves a digital footprint, indicating your interests, opinions, and writing style.
- Online Forms. Filling out online forms generates a digital record of your personal information, such as name, address, and other details. They include registration forms, survey forms, and subscription forms.
How to Delete Your Digital Footprints
If you frequently use the internet, it’s difficult to erase your digital footprints. The only possible way is going offline. It is also near impossible for most people, considering the current trend of business and workplace dependence on social media for various activities.
Limiting and being aware of the information you share online can help reduce and manage your digital footprints.
Digital Footprint Safety Tips
While it is impossible to eliminate your digital footprint, there are digital footprint safety tips to limit and hinder its growth. They include:
Prevent Tracking by Phone Number
Can someone track your location with phone number when you share it on different platforms? It is a question for many due to the increasing cybersecurity concerns, and unfortunately, the answer is yes.
You need to secure your device with safe cyber practices to prevent phone tracking. Here is what you should do:
1. Remove and Scan for Spyware
First, ensure you eliminate spyware from your devices to secure your privacy. Without this crucial step, your stalker can maintain unrestricted access to your location.
2. Check for App Performance
To check for permissions, turn off location services by swiping your phone down and tapping the location marker. Checking app permission ensures no app shares, records, or sells your data.
Here are the steps to follow when checking app permission:
- Go to Settings.
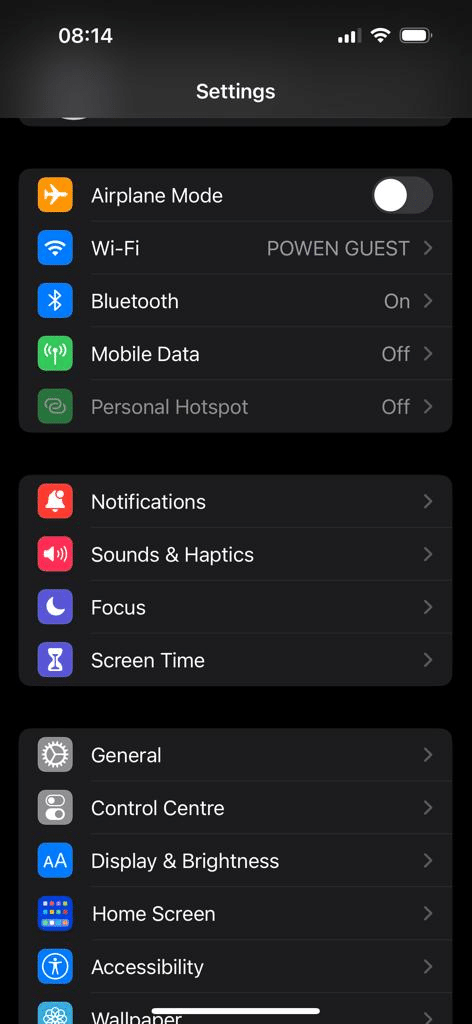
- Choose Privacy & Security.
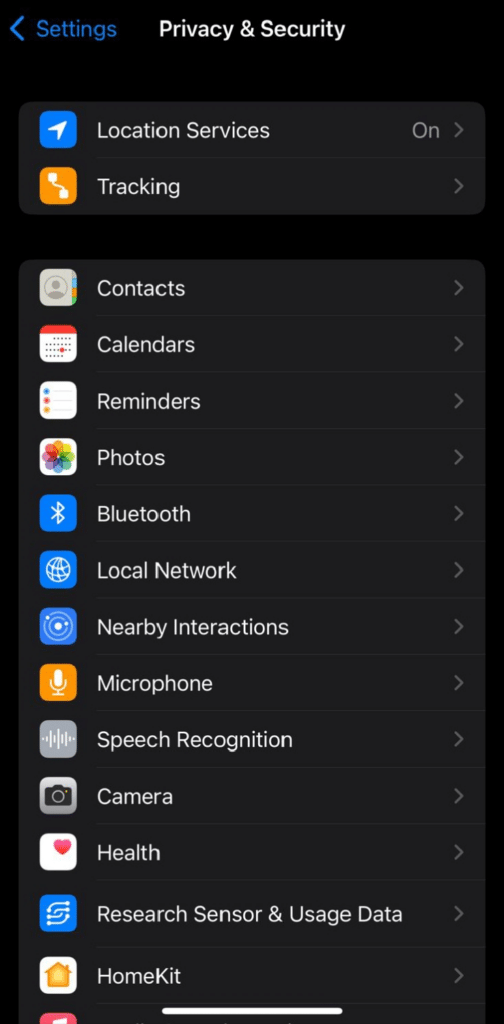
- Select Location Services and turn off location for privacy.
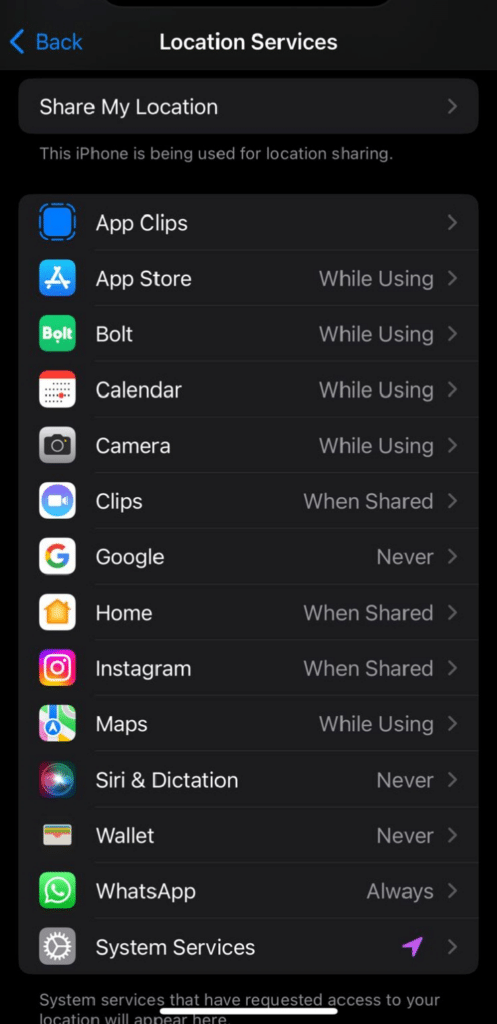
- Go to Settings > Privacy & Security.
- Click App Privacy Report to manage permissions.
- Eliminate unfamiliar apps.
When examining your app permissions, be attentive to unfamiliar applications. They could be spyware, compromising your personal information, or used for tracking and stalking. Also, be aware of fake apps that mimic legitimate ones.
If you’re unsure about some app on your device, reset it to the factory setting, and the non-system app will be removed. Always ensure you install apps from the official app stores. These are trusted apps that are scanned for malicious software.
4. Regular Software Updates
Keep your operating system, antivirus, and features that protect your system up to date. Your home’s Wi-Fi should also be updated to reduce exposure.
5. Strong Password Protection
Use strong, unique passwords for your accounts. Include a mix of letters, numbers, and symbols, and avoid using easily guessable information such as birthdays or common words.
6. Limit Social Media Interaction
Be mindful of the information you share on social media, as it can be used for social engineering attacks. Limit your exposure to “only friends“, remove your profile from public searching, and turn off the location button.
7. Monitor Your Online Presence
Regularly search for your name on search engines to see publicly available information. You should consider setting up Google Alerts for your name to receive notifications when new information about you appears online.
8. Be Careful of Unsolicited Emails
Avoid clicking on links or downloading attachments from unknown or suspicious emails. Always verify the sender’s identity before providing any personal information.
Consequences of Digital Footprint
The reasons you need to implement digital footprint tips is to avoid the following effects:
- Data breach: A digital footprint increases the risk of a data breach, exposing personal or sensitive information to unauthorized individuals or entities.
- Damaged reputation: A negative digital footprint, such as controversial online behavior or inappropriate content, can damage reputation, impacting personal and professional relationships.
- Fraud: A substantial digital footprint provides cybercriminals with valuable information for identity theft and financial fraud, putting individuals at risk of monetary losses and other related crimes.
- Blackmailing: Personal information shared online may be exploited for blackmail, as cybercriminals can threaten to expose sensitive details unless the victim complies with their demands, leading to potential emotional and financial harm.
- Cybersecurity risks: Large digital footprints increase vulnerability to cyber threats, including hacking, phishing, and other malicious activities targeting personal information.
- Employability impact: Employers often check digital footprints during hiring processes, and inappropriate online content can negatively affect professional opportunities.
Conclusion
Do not underestimate the importance of social media safety. By adopting privacy settings and exercising discretion in our online activities, you could avoid potential risks and protect yourself from unwanted scrutiny. Remember, your digital footprint reflects your identity, and managing it responsibly ensures a safer and more secure online experience.